
Sign up to save your podcasts
Or


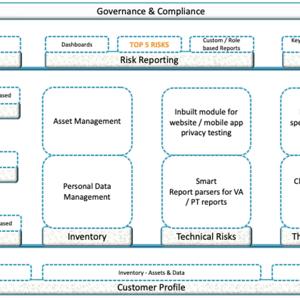

We now have the policies documented and approved. In this episode, we look at the step2 to design our Security Architecture. We need to design our Security Architecture so that the necessary controls within the policy are working adequately and giving us the sense of the security that we require.
Everyone equates Architecture design to a Technology and Product architecture. Actually, an architecture is much more. An architecture revolves around multiple areas as mentioned below
Organization Structure with roles and responsibilities
Re-defining the physical/network/digital layer to get more granular and segmented in terms of security. Identify various configuration that needs to be changed in the existing technology
Lastly and more importantly, upgrade/re-skill people skills. We need to keep in perspective that our people will be managing the systems and play an important role; therefore they need to be part of the process as well.
The flow described in this season can be used by in either of the below situations:
· you and work standalone/
· work with a consultant/expert
· can be used to run the show via the Arrka Privacy Management Platform (both for Security and Privacy).
For details, reach out to us on [email protected]; [email protected]; twitter: sameeranja, twitter: arrka2; Give a reference of this cast and avail credits on the platform usage and subscription. The Arrka Platform is made by SMB and for the SMB.
 View all episodes
View all episodes


 By Sameer Anja
By Sameer Anja
We now have the policies documented and approved. In this episode, we look at the step2 to design our Security Architecture. We need to design our Security Architecture so that the necessary controls within the policy are working adequately and giving us the sense of the security that we require.
Everyone equates Architecture design to a Technology and Product architecture. Actually, an architecture is much more. An architecture revolves around multiple areas as mentioned below
Organization Structure with roles and responsibilities
Re-defining the physical/network/digital layer to get more granular and segmented in terms of security. Identify various configuration that needs to be changed in the existing technology
Lastly and more importantly, upgrade/re-skill people skills. We need to keep in perspective that our people will be managing the systems and play an important role; therefore they need to be part of the process as well.
The flow described in this season can be used by in either of the below situations:
· you and work standalone/
· work with a consultant/expert
· can be used to run the show via the Arrka Privacy Management Platform (both for Security and Privacy).
For details, reach out to us on [email protected]; [email protected]; twitter: sameeranja, twitter: arrka2; Give a reference of this cast and avail credits on the platform usage and subscription. The Arrka Platform is made by SMB and for the SMB.