We heard in the previous episode about implementing various tools and technology configurations. We now have a reasonable set of preventive techniques working. This however, does not mean that we cannot be hacked our data cannot be stolen. To identify strikes and probes happening against us, we need to set up an alerting mechanism as well. This is an additional layer in our defense and should be potent enough to identify any attacks coming towards us.
Let us examine some scenarios to define alerts we require
Someone is running a vulnerability scan on our networks from outside to identify loopholes in our system. This is called Reconnaissance in the security parlance. It is a series of queries lobbied over the network and targeted at all systems exposed to the public internet. For this, our internet firewall needs to be configured to watch and report. Firewalls have the alert identified however we need to be able to see this.
Internal users have copied data marked as confidential to a USB disk. Anti malware etc software running on end point computers have the ability to detect, we need a system to process this and report/ alert.
Someone is trying to login using a brute force attack. A brute force attack is about running a sequence of characters designed to guess a password. We need systems to report/ alert all such login failures. A typical event matching algorithm will watch for login failures happening within a minute and alert accordingly. This may also be happening to our Administrator type users, and now the threat increases.
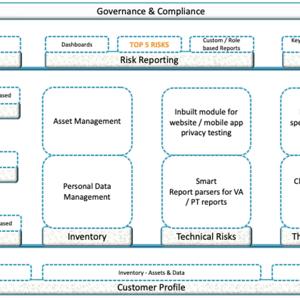
The flow described in this season can be used by in either of the below situations:
· you and work standalone/
· work with a consultant/expert
· can be used to run the show via the Arrka Privacy Management Platform (both for Security and Privacy).
For details, reach out to us on [email protected]; [email protected]; twitter: sameeranja, twitter: arrka2; Give a reference of this cast and avail credits on the platform usage and subscription. The Arrka Platform is made by SMB and for the SMB.