
Sign up to save your podcasts
Or


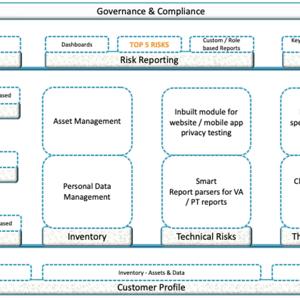

We have rolled out policies, procedures etc. However, it cannot be standalone and cannot be only a one-time review.
Review of implementations like Log Review, Incident Review, SIEM, Monitoring of the various access, set up a helpdesk etc. All of these can be implemented via Open Source solutions.
We have now defined policies, procedures, done the technical implementation using all the technologies we had within our setup. This is to ensure that we have generated optimum usage of everything we have spent on. Like learning, investment in technology is not wasted. We will always find use of this in every mode that is possible. Each desktop can be used, each laptop can be used in the defense of cybersecurity. It is not just the biggies like Firewall etc that come to the rescue. Many of the attacks happen through legitimate traffic (e-mail, while browsing) etc and hence the end point (as we call the desktop etc in security parlance) needs to have a defense mechanism as much as the others.
The flow described in this season can be used by in either of the below situations:
For details, reach out to us on [email protected]; [email protected]; twitter: sameeranja, twitter: arrka2; Give a reference of this cast and avail credits on the platform usage and subscription. The Arrka Platform is made by SMB and for the SMB.
 View all episodes
View all episodes


 By Sameer Anja
By Sameer Anja
We have rolled out policies, procedures etc. However, it cannot be standalone and cannot be only a one-time review.
Review of implementations like Log Review, Incident Review, SIEM, Monitoring of the various access, set up a helpdesk etc. All of these can be implemented via Open Source solutions.
We have now defined policies, procedures, done the technical implementation using all the technologies we had within our setup. This is to ensure that we have generated optimum usage of everything we have spent on. Like learning, investment in technology is not wasted. We will always find use of this in every mode that is possible. Each desktop can be used, each laptop can be used in the defense of cybersecurity. It is not just the biggies like Firewall etc that come to the rescue. Many of the attacks happen through legitimate traffic (e-mail, while browsing) etc and hence the end point (as we call the desktop etc in security parlance) needs to have a defense mechanism as much as the others.
The flow described in this season can be used by in either of the below situations:
For details, reach out to us on [email protected]; [email protected]; twitter: sameeranja, twitter: arrka2; Give a reference of this cast and avail credits on the platform usage and subscription. The Arrka Platform is made by SMB and for the SMB.